Key Points
Organizations are creating more entry points for attackers, according to our analysis of GreyMatter Digital Risk Protection data.
In the past six months, we recorded a 27% increase in customers’ exposed ports, a 35% rise in exposed operational technology (OT) ports, and twice as many exposed access keys.
Vulnerabilities in public-facing assets more than doubled, with 20-year-old flaws representing the most critical vulnerabilities identified.
CISOs must look beyond traditional security measures and address the external footprint—exposed credentials, open ports, and vulnerabilities. Proactively managing these exposures isn’t just important; it’s the frontline defense against external threats and a critical step in reducing the attack surface.
Every merger, technology rollout, or customer expansion represents progress to your investors—but to attackers, it means a bigger target. And they’re not wrong: Our Threat Research team conducted an in-depth analysis of GreyMatter Digital Risk Protection (GreyMatter DRP) data to find that enterprises’ external attack surfaces are expanding, creating more opportunities for adversaries to exploit.
We investigated customer alerts across 38 types of external exposures, comparing the second half of 2024 (July 1–December 31, 2024) to the first half of 2025 (January 1–June 30, 2025). Here’s what we found:
Exposed ports are multiplying: A 27% spike in exposed ports overall, with operational technology (OT) ports up by 35%. Each one is a potential entry point for attackers to authenticate to your services or exploit known vulnerabilities.
Typo-squatting remains a top threat: Threat actors like “Scattered Spider” use fake domains to impersonate brands and steal credentials. It’s still one of the most consistent and effective risks we see.
Decades-old vulnerabilities persist: Critical flaws dating back to 2006 are still appearing. Most affect web security technologies, like PHP and WordPress, with proof-of-concept (PoC) exploits circulating widely online.
As your organization grows, so does your digital footprint—and with it, your attack surface. With increasing reliance on digital channels for operations, communication, and data storage, adversaries have more opportunities to strike. Digital risk protection tools are essential for identifying and eliminating threats—ranging from leaked credentials on dark-web forums to vulnerabilities in public-facing assets—before they escalate into breaches.
In this report, we break down how adversaries are capitalizing on expanding digital footprints and what you can do to stop them.
The Same Exposures That Refuse to Disappear
The top five digital risks organizations face remained consistent from late 2024 into 2025. This stability reflects the ongoing effectiveness of attacker techniques and exposures caused by organizational practices—whether intentional or inadvertent.
July 1–December 31, 2024 | January 1–June 30, 2025 | ||
Risk Type | Percentage of Alerts | Risk Type | Percentage of Alerts |
Exposed Marked Document | 27.0 | Exposed Marked Document | 37.8 |
Impersonating Domain | 19.3 | Impersonating Domain | 19.0 |
Impersonating Subdomain | 13.4 | Impersonating Subdomain | 15.6 |
Evidence of Credential Access | 13.2 | Exposed Port | 10.2 |
Exposed Port | 7.1 | Credential Exposure | 4.6 |
Typo-Squatting Remains a Top Threat Because It Works
Criminal groups like Scattered Spider register impersonating domains and subdomains—a technique known as typo-squatting, to impersonate organizations and steal credentials. Our research found that technology vendors are prime targets, as a single fake domain can trick employees across multiple client organizations into providing their credentials. The earlier you catch these typo-squatted domains, the faster you can shut down phishing campaigns before they take hold.
Organizations Are Leaking More Sensitive Documents
Alerts for exposed marked documents jumped by over 10%, including customer information, network diagrams, internal policies, and help-desk procedures—data that attackers actively seek. While the exact cause of this increase remains unclear, many leaks stemmed from accidental exposures on organizations’ own websites. If left unaddressed, this data often ends up for sale on cybercriminal forums, where sellers sometimes claim to have breached the company. Such claims attract media attention and can lead to hefty regulatory fines, lawsuits, and significant brand damage.
Take Action
Stop typo-squatting in its tracks: Report malicious domains to registrars and hosting providers with clear evidence of infringement and block the root domain to prevent misuse. While bulletproof hosting may keep these sites online, blocking them can still mitigate their impact.
Track down and identify leaked data: Use OSINT techniques like Google search operators and reverse image searches to uncover leaked brand assets or confidentiality logos. Host or participate in vulnerability disclosure or bug bounty programs to empower security researchers to report discovered exposures of sensitive information. Regularly audit files uploaded to public web applications to ensure no confidential data is accessible.
Strengthen your workflows against social engineering attacks: Threat actors like Scattered Spider often impersonate vendors and IT support to obtain credentials. Train employees to identify these tactics and follow approved procedures for interacting with IT support and the appropriate communication channels.
Organizations Add 28 New Entry Points in Just 6 Months
Enterprise organizations need remote access, file transfers, and software connectivity to operate—but every service creates a potential entry point. Misconfigurations turn these necessary ports into attack vectors, and the numbers suggest the situation is worsening.
The average number of exposed ports per organization jumped from 103 in the last two quarters of 2024 to 131 in the first half of 2025—a 27% increase.
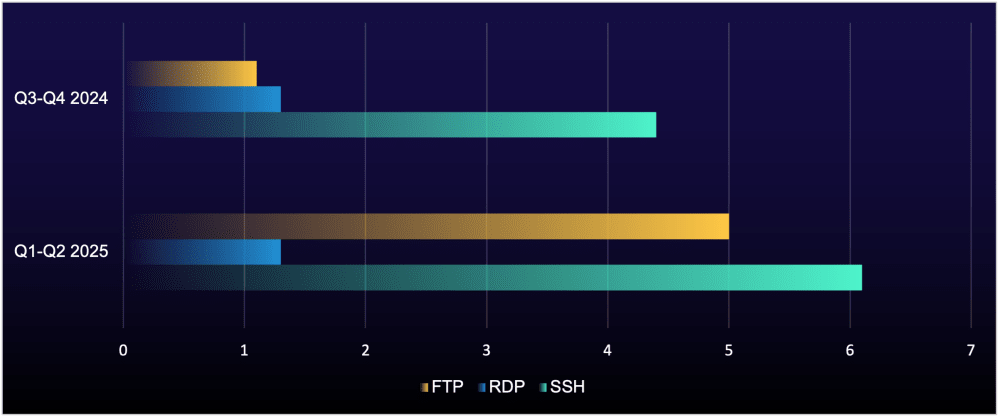
Figure 1: Average number of exposed risky ports per organization
The riskiest exposed ports are multiplying fast. File transfer protocol (FTP) and secure shell (SSH) exposures climbed throughout the first half of 2025.i Left unsecured, these ports can provide attackers with a direct path into an organization’s network—or serve as access that initial access brokers (IABs) package and sell to ransomware groups and their affiliates. Mergers, acquisitions, and the explosion of third-party remote support services are expanding attack surfaces faster than security teams can secure them.
This isn't just theoretical—we've seen it happen. In a recent intrusion, an attacker exploited an exposed Remote Desktop Protocol (RDP) login and gained initial access to an administrator account. They immediately attempted reconnaissance and lateral movement, but we isolated the compromised host before the attack escalated. Had the RDP port been identified and secured earlier, the entire incident could have been prevented. This highlights the critical importance of proactively identifying and securing exposed ports before attackers can exploit them.
Take Action
Scan public-facing assets: Proactively identify and assess exposed services. Consider disabling those that are not critical to business operations to reduce your attack surface.
Secure RDP access: Place systems using RDP behind a jump box secured with multifactor authentication (MFA) and require client device certificates to prevent unauthorized access.
Switch to key-based authentication for secure shell: Replace password-based authentication with SSH key pairs. This approach significantly reduces the risk of brute-force attacks on exposed SSH services.
Critical Systems at Risk: Exposed OT Ports Rise 35%
The surge in exposed ports is hitting OT for industrial control systems (ICS) especially hard.
The average number of exposed OT ports per organization grew by 35%, rising from 3.9 in the second half of 2024 to 5.3 in the first half of 2025.
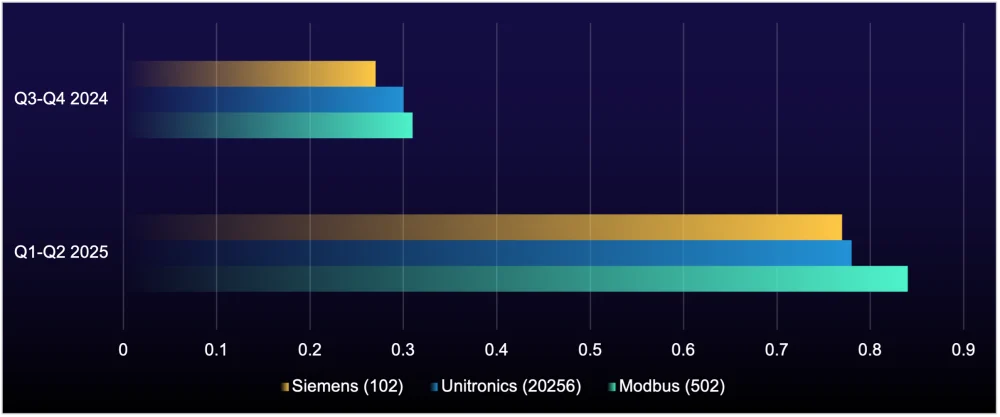
Figure 2: Average number of exposed OT ports per organization
Modbus (port 502) tops the list of the most exposed OT ports—particularly concerning given it has zero authentication. When exposed, attackers can execute unauthorized commands, overwhelm devices through denial-of-service (DoS) attacks, or exploit outdated versions. This then allows attackers to interact with—or shut down—programmable logic controllers (PLCs), remote terminal units (RTUs), and other critical OT systems.
We also saw a 160% uptick in the exposure of Unitronics port 20256, which has become a growing risk. For example, in response to the Israel-Hamas conflict, the Iran-linked threat group "CyberAv3ngers" targeted Israeli-manufactured PLCsii using this port (see Figure 3). Many of these exposed devices are connected to the internet with weak default passwords like "1111," making them easy targets.
Remote access and 24/7 monitoring are essential for ICS operations, but inadequate security measures introduce significant risks. Beyond data theft or financial loss, compromised OT systems can cause service disruptions across sectors, pose physical safety risks to workers and the public, and allow attackers to pivot into IT networks to target domain controllers and servers housing sensitive data.
The growing integration of smart technology into OT devices, their incorporation into IT networks, and their use of cloud services is likely driving this trend. As organizations accelerate connectivity, security teams are struggling to keep pace. Ideological adversaries are exploiting this gap, specifically targeting OT systems to maximize disruption and advance their political agendas.
Take Action
Secure OT network access: Remove OT devices from the public internet and secure remote connections through VPNs and jump servers. Enforce additional security measures such as MFA, geolocation restrictions, and device-based certificates.
Eliminate weak credentials: Audit all OT devices for weak or default passwords, especially those near the network edge. While ease of access may be necessary for some OT devices, prioritize securing these devices to mitigate password-guessing attacks.
Implement the Purdue Modeliii: Segment OT devices between security layers and subnetworks. Ensure all OT devices are not publicly accessible and properly segmented from the IT network by using demilitarized zones (DMZ) and firewalls to control network communications between each layer.
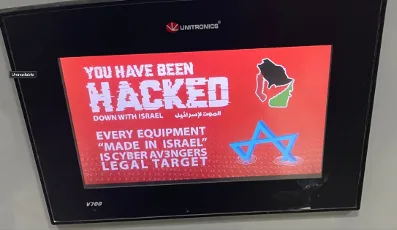
Figure 3: Image from post on Unitronics-related forum discussing PLC attack
19-Year-Old Vulnerabilities Are Still a Threat
Unpatched vulnerabilities in public-facing systems are a major risk, as attackers can gain access to on-premises networks, execute arbitrary commands on vulnerable web applications, or inject malicious code for full application takeover.
Vulnerabilities in public-facing assets more than doubled, rising from 3 per organization in the second half of 2024 to 7 in the first half of 2025.
July 1–December 31, 2024 | January 1–June 30, 2025 | ||
Severity | Vulnerability | Severity | Vulnerability |
Critical | CVE-2006-4812 | Critical | CVE-2008-4769 |
High | CVE-2012-2311 | High | CVE-2019-12765 |
Medium | CVE-2011-3368 | Medium | CVE-2016-8870 |
Low | CVE-2019-6263 | Low | CVE-2019-6263 |
To better understand the extent of this threat, we reviewed the most frequently identified vulnerability for each level of severity. Our analysis revealed that the most common critical vulnerabilities were CVE-2006-4812 and CVE-2008-4769, which date back nearly two decades and are still appearing on unpatched systems. These flaws enable full web application compromise via code execution and remain dangerous because PoC code is packaged into free penetration testing frameworks like Metasploit, enabling even novice attackers to automate exploitation.iv
Web applications handling customer payment information are particularly vulnerable to “Magecart” attacks, where adversaries inject malicious code to intercept credit card details in real time. Threat actors sell this malware through subscription-based “sniffer” services (see Figure 4), allowing lower-skilled attackers to carry out sophisticated attacks without developing the software themselves.
We also identified vulnerabilities in on-premises software like Server Message Block (SMB) services (CVE-2020-0796, aka SMBGhost) and Pulse Secure VPN servers (CVE-2019-11510). Just as we saw with Citrix Bleed 2, these flaws provide attackers with internal network access, creating pathways that lead straight to data theft and ransomware deployment.
Visibility into internal and public-facing technologies is a critical step in mitigating these risks. Comprehensive security solutions, like ReliaQuest GreyMatter Discover and GreyMatter DRP, provide security teams with a complete view of their assets and exposures across the organization’s attack surface, helping identify and mitigate threats inside and outside the network perimeter.
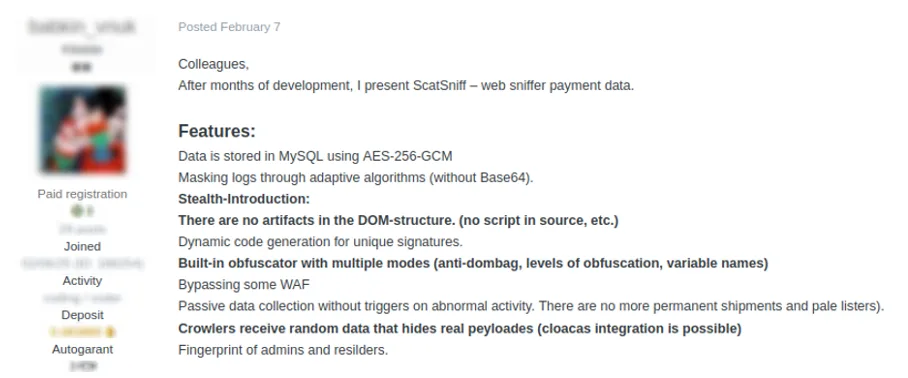
Figure 4: Cybercriminal forum member advertises sniffer malware for $1,000 USD (text translated from Russian)
Take Action
Shut the door on attackers: Prioritize patching public facing assets, including VPNs, which pose a significant risk if exploited because an attacker can gain access to the on-premises network.
Ensure web applications are secured: Regularly conduct web application penetration tests, as websites often have custom backend architecture that should be assessed to ensure security.
Block malicious traffic at the gate: Implement web application firewalls (WAFs) to detect and block attacks, including SQL injection and command injection attempts, to proactively protect applications.
Twice the Risk: Exposed Access Keys Double
Exposed credentials hand attackers the keys to your kingdom, allowing them to authenticate directly into your environment like legitimate users and bypassing the need for noisy phishing campaigns or exploiting vulnerabilities. And attackers aren’t just after usernames and passwords—cloud access keys and API keys are equally valuable targets.
From late 2024 to early 2025, the number of exposed access keys for organizations in our customer base doubled, creating twice the opportunity for attackers to slip in unnoticed.
July 1–December 31, 2024 | January 1–June 30, 2025 | ||
Risk Type | Percentage of Alerts | Risk Type | Percentage of Alerts |
Evidence of Credential Access | 13.2 | Credential Exposure | 4.6 |
Credential Exposure | 6.9 | Evidence of Credential Access | 3.2 |
Exposed Access Key | 0.5 | Exposed Access Key | 1.0 |
The increase in exposed access keys is likely tied to organizations typically beginning new cloud-related initiatives in January, resulting in increased development activity and more code pushes to repositories, rather than a shift in the cybercriminal landscape. Often leaked accidentally through code pushes to public repositories or shared on criminal forums and marketplaces, exposed access keys allow attackers to access organizations’ cloud environments for data theft, resource hijacking, and launching phishing campaigns from their own infrastructure.
Credential access alerts dropped significantly, almost certainly due to law enforcement actions against the most popular information-stealing malware (infostealer), “Lumma,” in May 2025v. With Lumma disrupted, attackers temporarily lost their primary tool for harvesting credentials from compromised customer devices (see Figure 4). However, by June 2025, new infostealers like "Acreed," "Vidar," and "StealC" began to fill the void, giving attackers fresh tools to dominate the market. This constant evolution forces defenders to adapt quickly; every time law enforcement disrupts one malware family, attackers simply pivot to another, leaving security teams scrambling to build new detections.
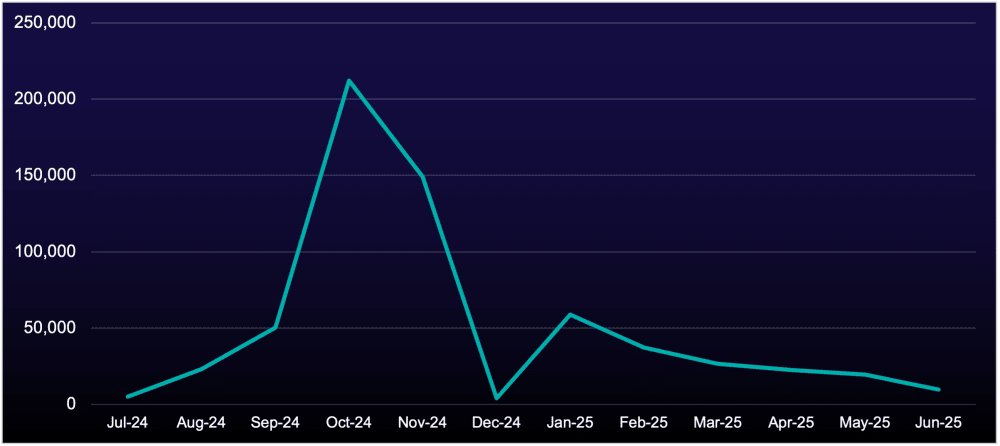
Figure 5: Number of Lumma log listings in GreyMatter DRP collection, July 2024–June 2025
Rates of credential exposure—when data gets leaked via third-party breaches or phishing attacks—saw a slight decrease. “BreachForums,” a cybercriminal forum used for sharing and selling stolen data from breaches, went offline in April 2025, temporarily disrupting the credential economy and likely contributing to the decline in this alert type. Exposed credentials provide attackers with easy access to on-premises systems, cloud environments, and third-party systems. So while defenders are focused on blocking attacks at the perimeter, attackers may already be inside using credentials that appear legitimate. By the time they’re detected, they could have operated unnoticed for weeks or months. The good news? You can beat them to the punch. Proactively identifying exposed credentials allows defenders to reset compromised passwords and rotate access keys before attackers’ cash in on them, ensuring your defenses stay ahead of exposed credential risks.
Take Action
Secure your keys: Use secrets management tools (e.g., AWS Secrets Manager and HashiCorp Vault) to safely store keys. Enforce pre-commit hooks to block sensitive data in code repositories, automate repository scanning with tools like GitGuardian or TruffleHog, and regularly rotate keys. Apply least privilege policies and train employees in secure coding practices, such as avoiding hard-coding keys.
Ditch browser password storage: Storing passwords in web browsers makes them vulnerable to infostealers. Encourage the use of secure password managers to store credentials, which encrypt credentials and significantly reduce the likelihood of attackers accessing sensitive information in the event of malware compromise.
Disallow personal devices for work: Personal devices lack enterprise-grade protections like EDR, increasing malware risks. Enforce policies requiring the use of company-managed devices with proper security measures and educate employees on the risks of using personal devices for work-related tasks.
Key Takeaways and What’s Next
Organizations are juggling more systems than ever, and each new technology deployed expands the attack surface. Without proactive measures, misconfigurations, visibility gaps, and sensitive data leaks leave the door wide open for attackers to compromise networks.
To mitigate these risks, organizations must think like an attacker: Assess internet-facing exposures, hunt for leaked sensitive data, and identify weak points adversaries can exploit. Proactive defense is often deprioritized but can make the difference between a minor incident and a full-blown breach.
Looking ahead, we predict that organizations' external attack surfaces will continue to evolve:
IoT Will Expand Attack Surfaces
The number of smart devices, also known as the Internet of Things (IoT), grew to 17.7 billion by the end of 2024 and is projected to reach 31.2 billion by 2030.vi These devices are notoriously vulnerable, with common weaknesses like default credentials and coding errors that can enable remote code execution (RCE). As IoT devices multiply, organizations’ attack surfaces will expand, giving attackers new avenues to exploit weaknesses.
AI Brings New Opportunities
The rapid adoption of AI is outpacing security measures, giving rise to risks such as prompt injection attacks, exposed pre-production environments, and leaked credentials for the backend of AI systems—each of which can provide attackers with unauthorized access to sensitive data. AI not only presents a new target for adversaries but introduces significant risks for businesses tied to the underlying software, potentially exposing organizational and customer data to breaches.
Credentials and Vulnerabilities: The Ultimate Skeleton Key
With on-premises systems becoming harder to penetrate through traditional access methods like phishing with trojan-laced emails, attackers are increasingly relying on stolen credentials and exploiting internet-facing vulnerabilities. The booming infostealer malware market and the rise of social engineering tactics from Scattered Spider and “Black Basta” highlight this shift. Meanwhile, ransomware-as-a-service (RaaS) affiliates and closed ransomware groups like “Clop” and “Inc Ransom” are increasingly exploiting vulnerabilities in internet-facing devices that offer limited logging and detection capabilities.
Now more than ever, organizations need a clear view of their external risks. Proactively identifying and addressing risks like exposed credentials and vulnerabilities with solutions like GreyMatter DRP empowers defenders to mitigate threats before attackers can exploit them, helping organizations build a more resilient security posture.


